Microsoft Active Directory, in all its variations, can be considered one of the most widely-used identity and access management services by businesses today. It is a critical foundational component for companies adopting Microsoft services and solutions both on-prem and in the cloud.
In this article we are going to explore how managed service providers (MSPs) and businesses can take advantage of their existing users and groups created in Active Directory to create a powerful and robust policy-based web filtering and application control solution, through integration with Zenarmor®, providing granular control over which applications and web traffic is allowed to traverse the network.
One of the most significant advantages of leveraging Zenarmor integrated with Active Directory is that MSPs and businesses alike can almost instantly satisfy corporate and internet usage security policies and in some industry-specific circumstances even satisfy governmental regulatory compliance requirements such as the Children’s Internet Protection Act (CIPA) which is applicable in educational environments like schools, universities, and libraries.
As a side note, if you are interested in why Zenarmor is the perfect content-filtering solution for educational institutions please take a look at a previous article that I wrote covering this topic in more detail.
For this article, to showcase how this solution works, I have created a basic network that includes an OPNsense firewall with Zenarmor installed and registered with the Zenconsole cloud-based dashboard. In addition to this is a server running Windows Server 2019 that has been set up and promoted to an Active Directory Domain controller. And finally, I set up a Windows 11 desktop machine joined to the domain that will be used for testing purposes.
I modeled this demonstration around a typical school campus network, however, school and business networks share an almost identical design, so a solution like this can be adapted and scaled easily to fit your unique requirements.

Figure 1: Desktop view of the Windows Server 2019, showing the already setup domain controller and the Students and Staff security groups including some students and staff users as group members of their respective groups for testing purposes
Downloading and installing the AD Agent
To make the integration of Zenarmor and Active Directory possible, you will need to install a lightweight agent on your domain controller, a service that periodically updates Zenarmor about domain users and groups via the Zenarmor API.
The agent installation is straightforward, you will need to head over to https://www.zenarmor.com/get-ad-agent and download the .zip file. Unzip the archive and run the setup.exe as an administrator. Simply follow the prompts and complete the setup.

Figure 2: Desktop view of the Windows Server 2019, showing the extracted zip file containing the AD agent installer package
How to Configure Zenarmor AD Agent?
Once the agent has been installed the configuration process is very simple. To start, If you have installed Zenarmor on your OPNsense firewall as I have, you will need to access your OPNsense dashboard and go to the Zenarmor configuration menu, under the general tab, you will need to scroll down to the section titled AD Agent Authentication Token(s) and click the “Create New Token” button.
Be sure to copy your newly created token because you will need it when setting up the AD agent on your domain controller.
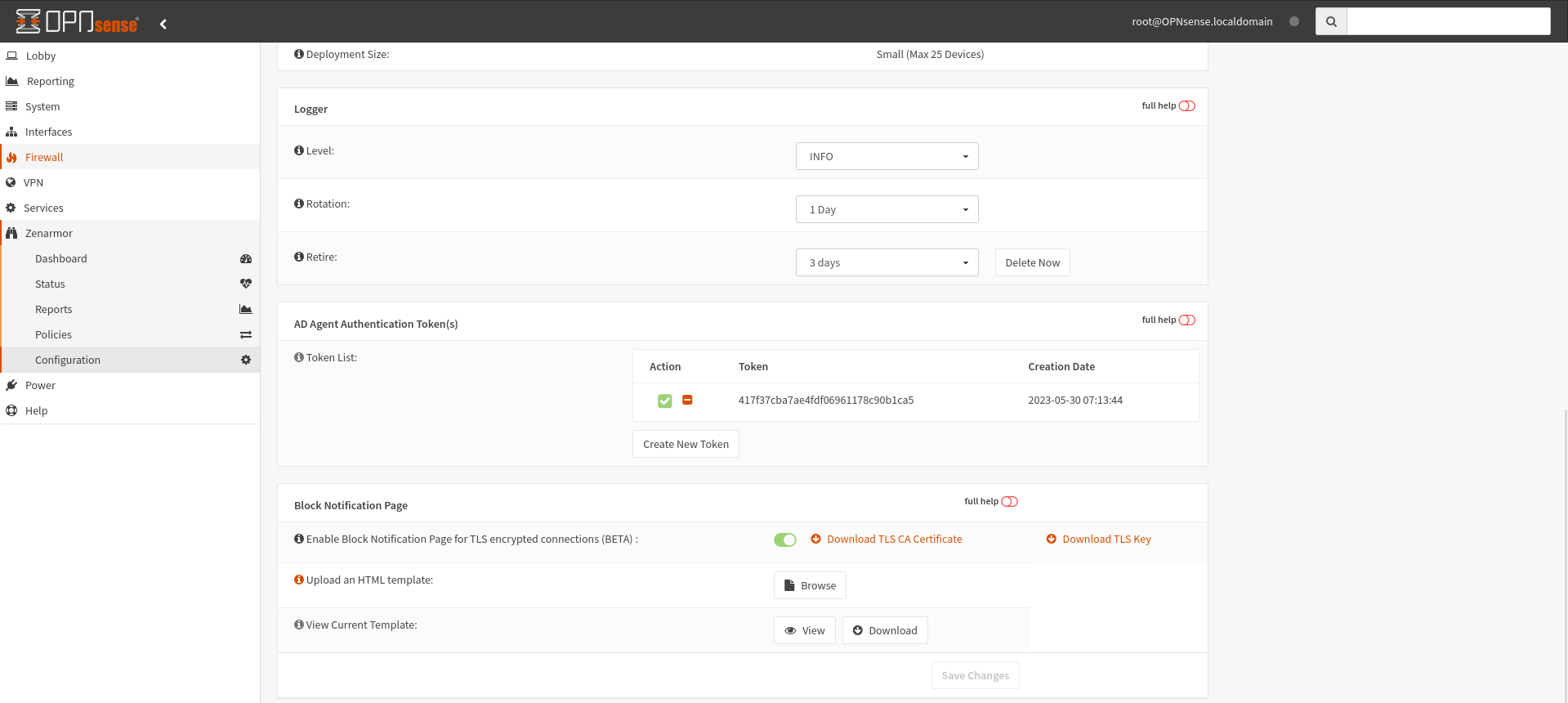
Figure 3: OPNsense dashboard showing the Zenarmor Configuration menu where the AD token is created under the General tab.
On your domain controller, open the Zenarmor Active Directory Agent that you previously installed, and firstly choose your platform, in this case, OPNsense. Below that enter the IP address or domain name of your OPNsense firewall including the https:// prefix before the IP address/Domain name and leave the port as 443. The agent communicates via HTTPS with the OPNsense firewall API. Finally, copy the AD token that you created in the previous step into the API Token textbox and click the “add host to list” button below.
Ensure you toggle the service status button to “running” and click save. Your agent will now communicate with the firewall if all was successful. If you have any machines in your domain that you don’t want to share with Zenarmor, you can simply add those to the excluded hosts section. The log level can be left as is, however, this is entirely your preference and may come in handy when debugging if the need arises.
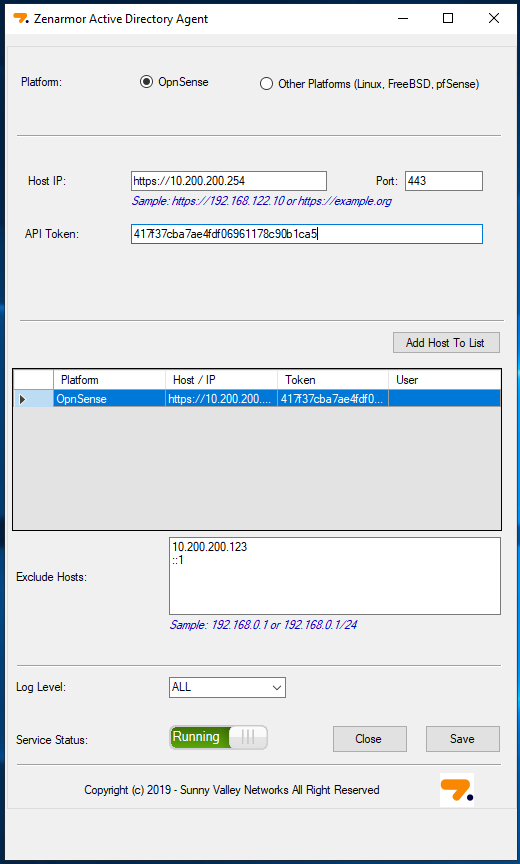
Figure 4: Zenarmor Active Directory Agent configuration for OPNsense integrations
If you have installed Zenarmor on another operating system like Ubuntu, RedHat, or pfSense, there is a slightly different configuration required. Firstly, you will need to use your Zenconsole dashboard to enable and create the API key. Select your firewall and go to the settings page, and at the extreme bottom of the page, you will see API. You need to enable the API functionality by clicking the “Disabled” toggle button on the extreme right and once enabled you can click the “Generate API Key” button.
You will be prompted to enter a user, in this case, I just called mine “activedirectory” and then you click “generate”. Remember this username as you will need it when we configure the AD agent on the domain controller.
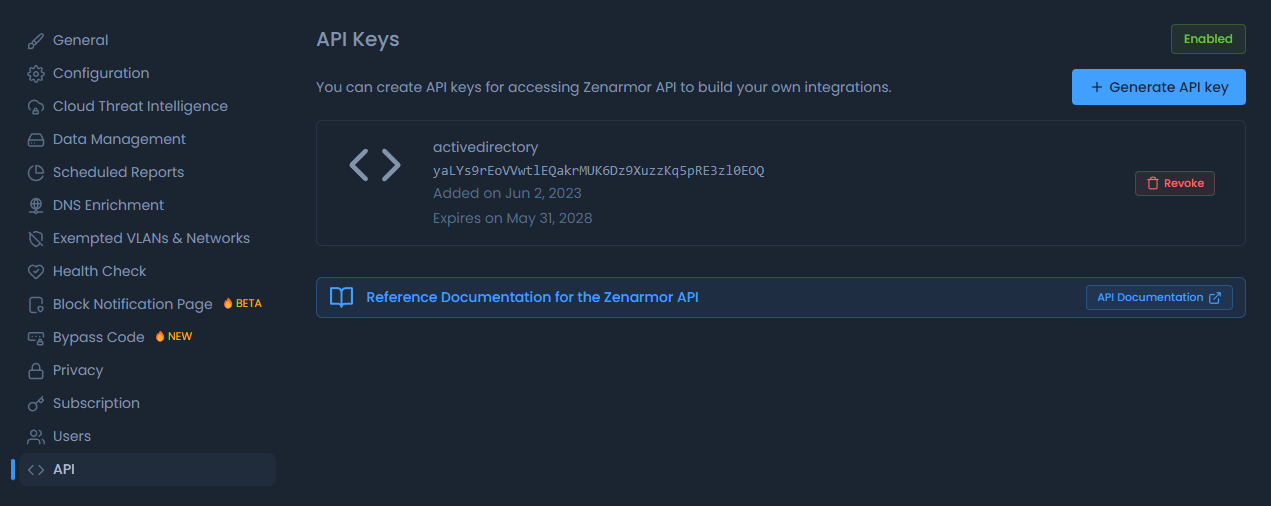
Figure 5: Zenconsole API key generation menu
You will now need to open the AD agent on your domain controller and like we did for OPNsense, add the host ip, the API key you just generated, and the user of the API key. Once done click “Add host to List” and “Save” and you have now integrated your AD with Zenarmor.
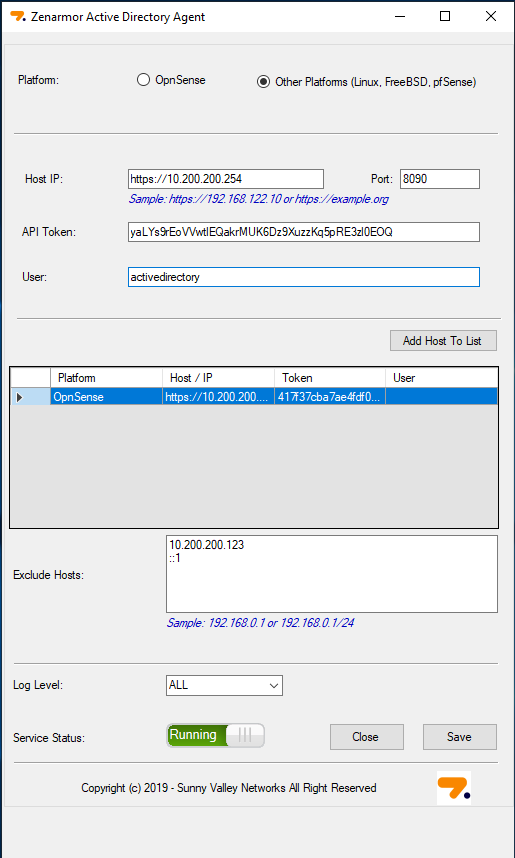
Figure 6: Zenarmor Active Directory Agent configuration for other operating system integrations.
On another side note, if you are interested in learning how to deploy Zenarmor on Ubuntu Server 22.04 in an L2 bridged deployment mode, feel free to have a look at a video I created showcasing this topic, alternatively, you can see this blog post.
Using Active Directory Users and Groups in your Zenarmor policies
Now that Active Directory has been integrated with Zenarmor we can create policies that filter traffic by AD Users and Groups. If you recall at the beginning of this article I mentioned creating two security groups, Students and Staff. For this scenario, we are going to create two Zenarmor policies one for Students where we will be blocking all social network traffic, and a second policy for staff blocking online shopping sites and applications.
Creating new policies in Zenarmor is very straightforward, you will select the policies menu option and select the “create new policy” button. You will need to name your policy and then complete the initial configuration, you can refer to the screenshot below.

Figure 7: Zenarmor policy creation – Student policy status has been enabled and filtering options have been set to filter by IP/Networks which in this case is 10.200.200.0/24, the LAN network and under Groups I have added Students, the name of the security group configured in the Active Directory.
Just something to note when creating your policies, policies are ordered and filtered from the TOP down and the default policy will always be on the bottom of the stack which catches all the traffic that did not get filtered by the policies above it. Also, keep in mind that when filtering by VLANs, IP/Networks, MAC Addresses, and Users and Groups that this process uses AND logic, so basically, ALL the filtering conditions you selected need to be true or the traffic will bypass the policy.
So, to see the policy-based filtering in action, I logged into the Windows 11 desktop with the student1 user that is a member of the Students security group, and opened the browser. I then navigated to twitter.com and as expected, Zenarmor intercepted this communication and prevented the user from accessing the social networking website as seen in the screenshot below.

Figure 8: Zenarmor blocked landing page showing that the communication with twitter.com from the student1 user account has been intercepted and blocked.
The same would apply if we browsed the web with one of the staff members’ accounts, where in their case, access to online shopping would be blocked. The beauty of this setup is that we have had no need to configure any proxy servers or settings, Zenarmor has accomplished web filtering and application control in a fraction of the time it would take to set up a proxy server, all using existing AD users and groups.
Some final words…
Are you ready to try this Zenarmor integration yourself? If you would like to get your feet wet and explore policy-based web and application filtering and the many other great capabilities of Zenarmor, try Zenarmor on a 15-day trial, with no credit cards required.