In a previous blog article, we explored the concept of using Zenarmor® as a cloud-deployed secure web gateway (SWG) as part of a Secure Access Service Edge (SASE) architecture, where Zenarmor® was set up inline to filter egress internet traffic. Today, we are going to take a deeper look at the Layer 2 bridge deployment mode available with Zenarmor® and how it can be used to build a similar inline or transparent security gateway. Because Zenarmor® is totally software-defined with zero hardware dependency, you have the ultimate choice and control over how you would like to deploy Zenarmor®.
For this article, I have chosen to use Ubuntu server 22.04 because of its popularity and general ease of use, however, with minor adaptions you can easily use this tutorial with other popular Linux/Unix-based operating systems including, but not limited to, CentOS, FreeBSD, RedHat and Amazon Linux.
Why would you consider Layer 2 bridge mode instead of Layer 3 routed mode for your Zenarmor® deployment?
If you have been following Zenarmor® for a while, you probably came to know about it through the OPNSense firewall project available as a next-generation firewall plugin. When installing Zenarmor® using the plugin on OPNSense, the deployment mode will default to Layer 3 routed mode because this allows you to benefit from both Zenarmor® and other OPNSense services like routing, filtering, VPN, and proxy which in most cases is why people deploy OPNSense anyway.
But what if you are already happy with your current Linux router setup or add OPNSense to your network creating a double NAT scenario. Maybe you simply don’t have extra hardware lying around to build an OPNSense firewall. Perhaps your requirements are to protect your cloud infrastructure using Zenarmor® and simply need a transparent secure gateway solution. Regardless of the reason, Zenarmor® deployed in Layer 2 bridge mode gives you all the great benefits of Zenarmor® such as filtering, blocking, and reporting on your existing Linux router platform.
How to create a network bridge in Ubuntu 22.04?
For this tutorial, I have set up a fresh copy of Ubuntu server 22.04. Installed in this server are two network adapters, one plugged into the LAN switch, and the other plugged into an existing router connected to the ISP. This router provides IP addresses to LAN devices using DHCP.

Figure 1: Network topology that we are creating in this tutorial
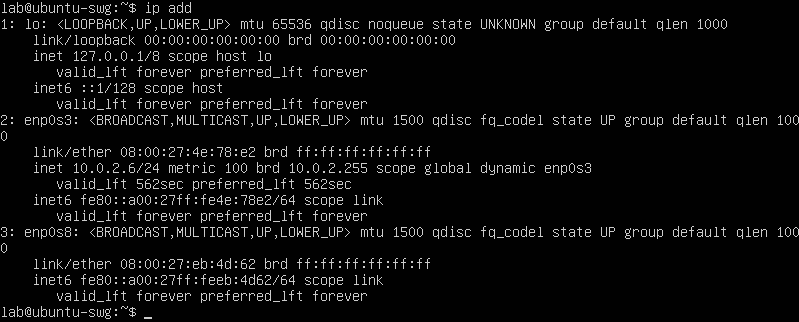
Figure 2: Two network interfaces, enp0s3 connected to WAN router, enp0s8 connected to LAN switch. enp0s3 received a 10.0.2.6/24 IP address from the router via DHCP.
Without the bridge interface setup on our server, you will notice that only the Ubuntu server will have internet connectivity while the LAN will be cut off from the internet. Let’s fix this by creating the network bridge.
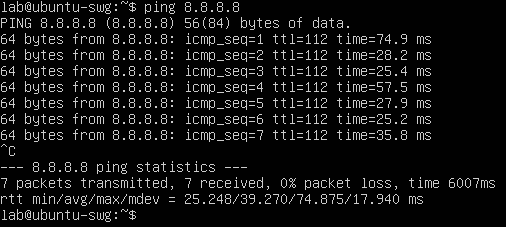
Figure 3: Ubuntu server is able to ping the internet.
There are various methods that you could use to create a network bridge in Ubuntu, however, for this tutorial, I have chosen to use Netplan which is a utility that easily allows you to configure networking on Linux systems by simply using YAML to describe your network configuration.
Netplan by default creates this configuration YAML file in /etc/netplan and in my case was named 00-installer-config.yaml
To make changes to this YAML configuration we are going to use the nano text editor, it’s my preference, however, you can also use VIM if you prefer.
Type into the command line:
sudo nano 00-installer-config.yaml
and hit enter and enter your password.
Your configuration should look similar to the one in the image below. enp0s3 is connected to the WAN and has DHCP enabled whereas enp0s8 connected to the LAN is currently not configured.
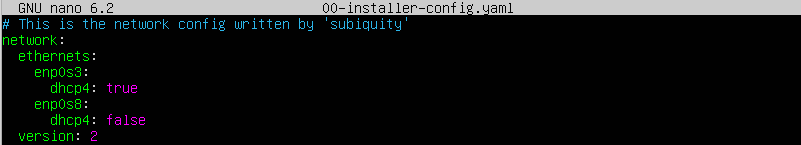
Figure 4: Example of the 00-installer-config.yaml configuration
To create the bridge, we need to first modify this configuration by disabling DHCP on both interfaces and add the following below the version section:
bridges:
br0:
dhcp4: true
interfaces:
– enp0s8
– enp0s3
This tells Netplan to create a bridge interface called br0, enables DHCP on the interface, and joins both enp0s8 and enp0s3 to the bridge.
Your final configuration should look like the below image:
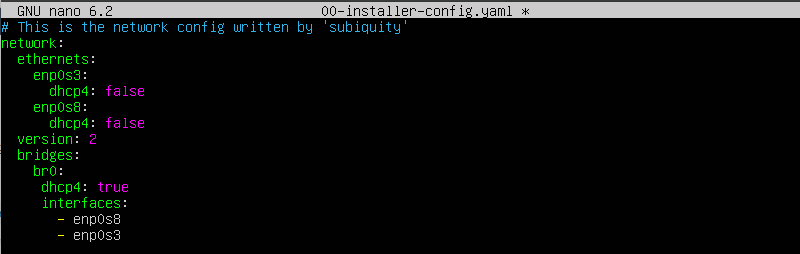
Figure 5: Updated 00-installer-config.yaml configuration including the bridge interface.
Next type ctrl+x and then type ‘Y’ to save the configuration. We then need to apply the new Netplan configuration by typing:
sudo netplan apply
If all went well the br0 interface will now be active, you can confirm this by typing ip add and you will see a similar output to the one below showing br0 with the IP address of 10.0.2.4/24. Your server and devices on the LAN will now both have internet connectivity via the bridge.
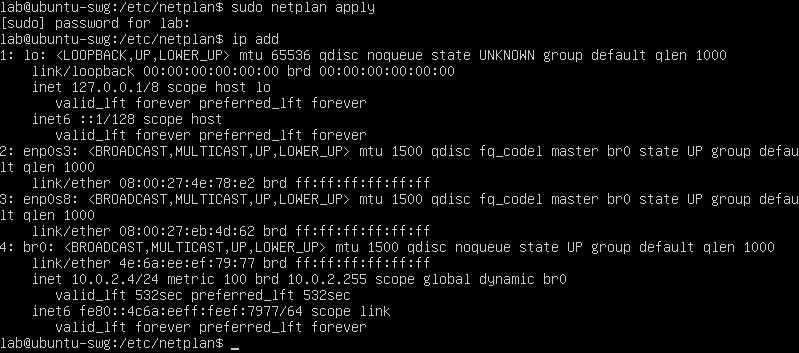
Figure 6: Output showing the br0 interface as active
How to install and configure Zenarmor® on your Ubuntu 22.04 server?
So now that we have the network setup out of the way, let’s continue with the quick and easy part, installing Zenarmor®.
First, run the below command and follow the prompts, this will automatically install Zenarmor® on your server:
curl https://updates.sunnyvalley.io/getzenarmor | sudo sh
While Zenarmor® is being installed on your server, go to https://dash.zenarmor.com/login and signup for a free account so that you can access the Zenconsole dashboard that we will be using in the next steps to finalize and manage the Zenarmor® installation.
The final step once Zenarmor® has finished installing, is to register with the Zenconsole dashboard by simply typing the below command and using the email address and password that just used during the sign-up process:
sudo zenarmorctl cloud register
Figure 7: Registration process
If all went well you have just successfully installed Zenarmor® and connected it to the Zenconsole dashboard, it’s really this quick and easy.

Figure 8: Visual summary of the Zenarmor® installation process
Next, you will need to log in to Zenconsole to complete the Zenarmor® configurations. Once there, go to “My Firewalls” and you should see the Ubuntu server that we just registered

Figure 9: Zenconsole showing firewall configuration
You will need to give your firewall a name, I called mine Ubuntu SWG.
Next, choose your desired reporting database type, for this tutorial, I am using SQLite, however, you also have the option to connect to an Elasticsearch database if you wish, this is generally best for larger deployments.
The deployment mode we are using is Bridge Mode so select that option.
Then finally, at the bottom of the page, select both your interfaces enp0s3 and enp0s8, and assign the security zones, one being LAN and the other WAN. Then click the “Add Firewall” button.
You will then be redirected back to the home page of the dashboard where you will see the newly configured firewall like in the image below.

Figure 10: Zenconsole home dashboard listing all firewalls and providing a general overview
You have now successfully installed Zenarmor® in Layer 2 bridge mode on Ubuntu 22.04! From here on you are ready to start creating your security policies and enjoying the immediate benefits Zenarmor® has to offer.
So what are you waiting for, if you haven’t done so already, sign-up and try Zenarmor® on a 15-day Business Edition trial today!